LimePoint can help you deploy complex platform solutions to meet regulatory and compliance requirements. For example, we helped a client secure an on-premise InfluxDB Enterprise cluster with AzureAD-integrated RBAC by implementing fine-grained authorisation over LDAP (Lightweight Directory Access Protocol).
In this post, we will look at configuring LDAP in InfluxDB at a high level with some deep dives into the complicated aspects.
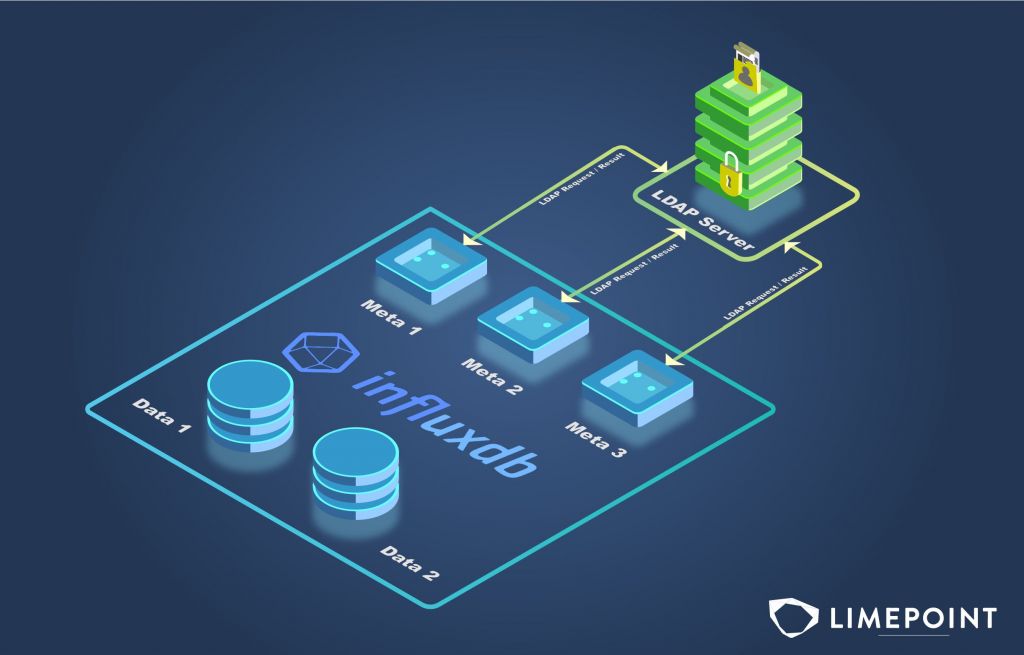
Metanode & Raft db
Metanode stores metadata, including authentication data, in a Raft database on disk. Enabling LDAP involves setting the configuration on the meta config files as well as separately on the Raft db.
The following are the high level steps:
- Enable ldap auth in the meta node config files on all nodes ({influxdb-config}/influxdb-meta.conf)
- Create LDAP config file (generate sample file using influxd-ctl)
- Verify the LDAP config file (again using influx-ctl)
- Apply the LDAP config file on any one meta node (using influx-ctl. This sets the value in the Raft db)
It seems straightforward. However, some gotchas can make this deployment quite complex.
Sample LDAP configuration for a quick start
# Sample TOML for ldap config.
# First, save this file and edit it for your LDAP server.
# Then test the config with: influxd-ctl ldap verify -ldap-config /path/to/ldap.toml
# Finally, upload the config to the cluster with: influxd-ctl ldap set-config /path/to/ldap.toml
#
# Note: the meta nodes must be configured with meta.ldap-allowed = true
# and the data nodes must be configured with http.auth-enabled = true
enabled = true
[[servers]]
host = "ldap.example.com"
port = 389
# Credentials to use when searching for a user or group.
bind-dn = "cn=read-only-admin,dc=example,dc=com"
bind-password = "read-only-admin's password"
# Base DNs to use when applying the search-filter to discover an LDAP user.
search-base-dns = [
"dc=example,dc=com",
]
# LDAP filter to discover a user's DN.
# %s will be replaced with the provided username.
search-filter = "(uid=%s)"
# On Active Directory you might use "(sAMAccountName=%s)".
# Base DNs to use when searching for groups.
group-search-base-dns = ["ou=groups,dc=example,dc=com"]
# LDAP filter to identify groups that a user belongs to.
# %s will be replaced with the user's DN.
group-membership-search-filter = "(&(objectClass=groupOfUniqueNames)(uniqueMember=%s))"
# On Active Directory you might use "(&(objectClass=group)(member=%s))".
# Attribute to use to determine the "group" in the group-mappings section.
group-attribute = "ou"
# On Active Directory you might use "cn".
# LDAP filter to search for groups during cache warming.
# %s will be replaced with the "group" value in the group-mappings section.
group-search-filter = "(&(objectClass=groupOfUniqueNames)(ou=%s))"
# Attribute on group objects indicating membership.
# Used during cache warming, should be same as part of the group-membership-search-filter.
group-member-attribute = "uniqueMember"
# Groups whose members have admin privileges on the influxdb servers.
admin-groups = ["influx-admins"]
# Mapping LDAP groups to Influx roles.
# All Influx roles need to be manually created to take effect.
[[servers.group-mappings]]
group = "app-developers"
role = "app-metrics-rw"
[[servers.group-mappings]]
group = "web-support"
role = "web-traffic-ro"1. Use JWT secret when working with LDAP
You could get away with basic auth when verifying and setting the config.
influxd-ctl -auth-type basic -user admin -pwd admin ldap verify -ldap-config ldap-config.toml
influxd-ctl -auth-type basic -user admin -pwd admin ldap set-config ldap-config.tomlBut once its in the Raft db, you’ll need to use jwt for the influxd-ctl commands. The auth-type of “basic” doesn’t work when ldap is configured.
influxd-ctl -auth-type jwt -secret "mysupersecretstring" show2. Disabling the ldap config is a multi-step process
From the meta node, edit ldap config file and set
enabled = falseVerify syntax and then load the config into the raft database
influxd-ctl ldap verify -ldap-config ldap.toml
influxd-ctl ldap set-config ldap.tomlThen disable LDAP in each meta-node’s config file (/etc/influxdb/influxdb-meta.conf)
meta.ldap-allowed = falseAnd then restart Influx on each node
service influxdb-meta restart3. Group membership search filter
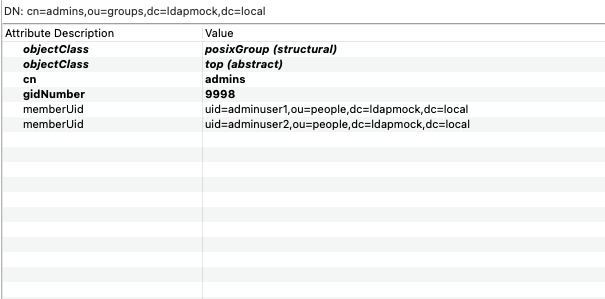
InfluxDB authentication code MUST use the dn, and not the cn field when looking for group membership. This means the search filter to the LDAP server should look like “(memberUid=uid=adminuser1,ou=people,dc=ldapmock,dc=local)” where uid=… is the dn.
filter="(&(objectClass=posixGroup)(memberUid=uid=adminuser1,ou=people,dc=ldapmock,dc=local))"Below are screenshots from the LDAP server. The first one below shows the expected structure “dn” for the search attribute, which is “memberUid” in this example.
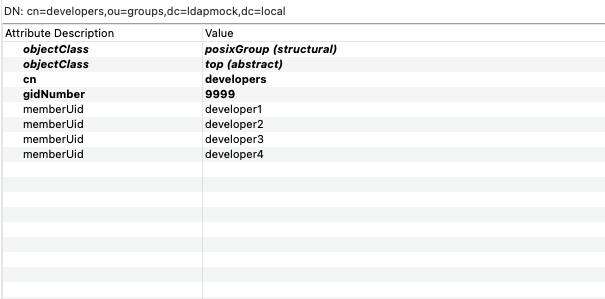
Below is an incorrect structure with just the “cn” (developer1) in the search attribute.
4.Warming up the LDAP cache
The ldap warm-cache command is your friend when you suddenly start seeing 403 errors and unauthorized errors inconsistently on a datanode.
influxd-ctl -auth-type jwt -secret mysuperscretstring ldap warm-cacheConclusion
Navigating the complexities of securing InfluxDB Enterprise doesn’t have to be a solitary journey. Whether you’re just starting out or looking to optimise an existing setup, LimePoint offers the expertise and support to ensure your deployment meets the highest standards of security and compliance.
Have questions or need personalised assistance? Contact LimePoint today for a consultation and discover how we can help streamline your platform solutions.

