Overview
For companies who are existing clients of LimePoint, installing DriftGuard in the AWS Cloud can be a very quick and simple exercise thanks to AWS CloudFormation (CFN). New clients can also follow this procedure of course, once access to releases and licencing has been sorted.
Like a previous blog post documenting how to install DriftGuard on AWS, this process involves provisioning both EC2 and RDS instances, however, this time around we’re demonstrating how to complete this by simply deploying an AWS CloudFormation template. The whole process takes around 15 minutes, at the end of which, you have a functioning DriftGuard environment.
In contrast to the previous blog, no real AWS experience is necessary in order to complete the required steps. Requirements still include access to an AWS account (with permissions to create and manage EC2 and RDS components), and access to DriftGuard releases, and a valid licence.
It should be noted that the Security Group in this example has deliberately been configured to be open to any IP, but in secure environment this should be locked down appropriately.
The Keypair created as part of this process is not actually required for login at any point, however, if the server is created without a keypair specified, it will not be possible to log into the server at any future point.
The high-level steps are as follows:
- Create Keypair
- Create CloudFormation Stack
Create Keypair
- Navigate to the EC2 Dashboard console
- On the left, under ‘Network and Security’, click ‘Key Pairs’
- Click ‘Create key pair’
- Enter key pair name “dg” – leave “pem” selected
- Click ‘Create key pair’
- From the dialog box that appears, save the key pair to your workstation
Create CloudFormation Stack
- Save the Template in the Appendix to a file on your local machine
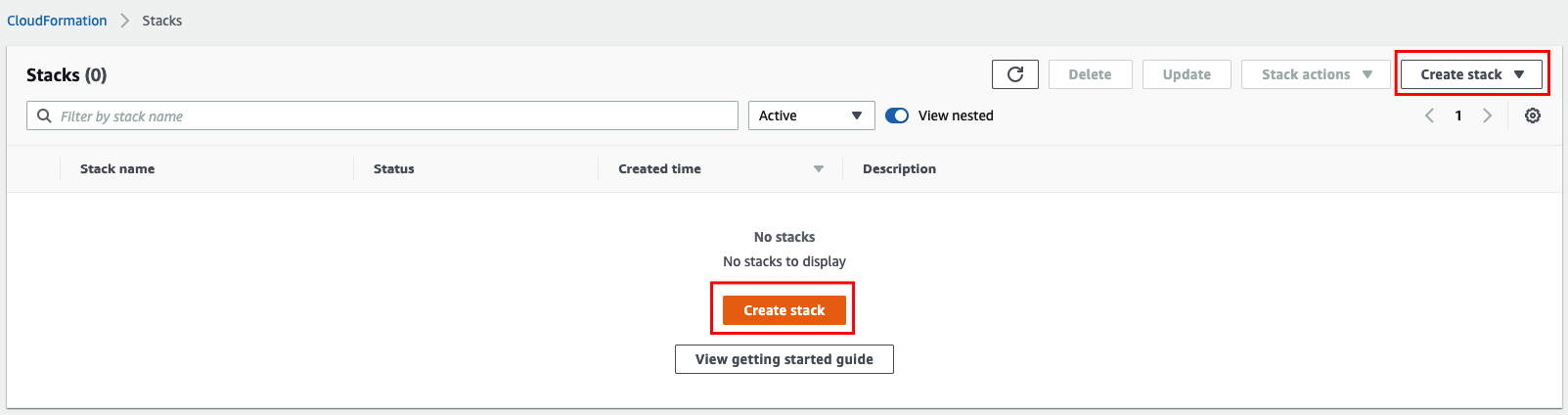
- Navigate to the CloudFormation Dashboard console
- Click ‘Create Stack’

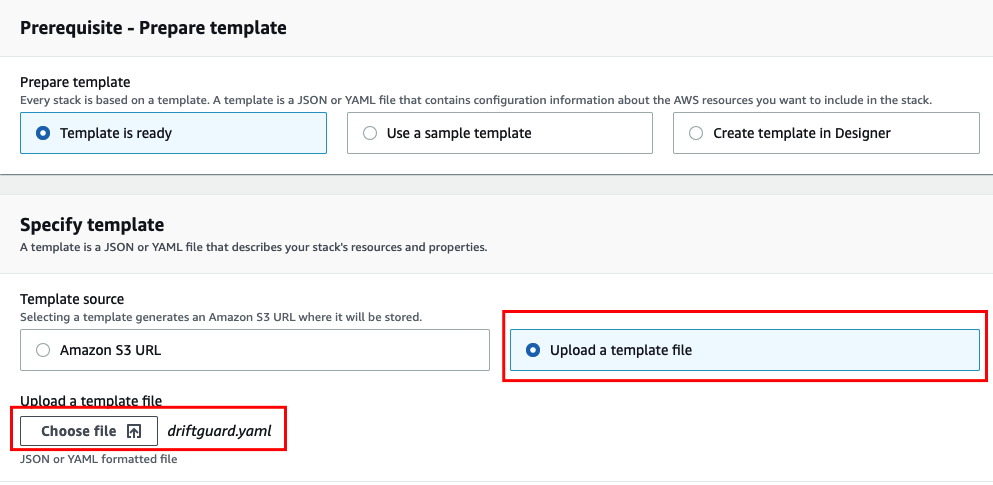
- Select the option to ‘Upload a template file’
- Click ‘Choose file’, select the file you created in Step 1, and click ‘Next’

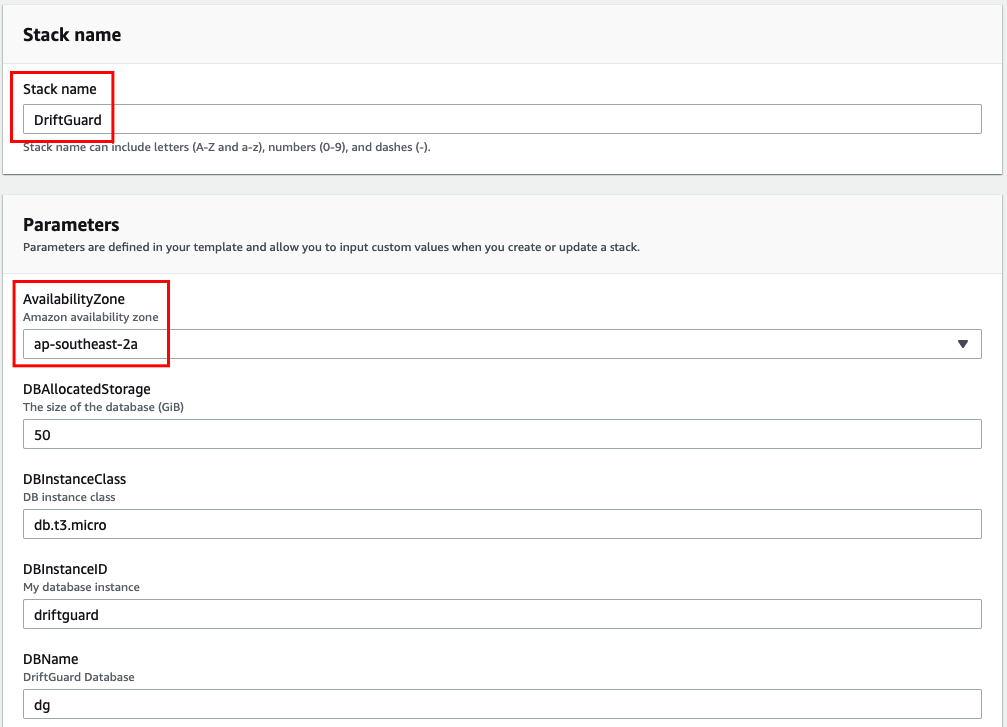
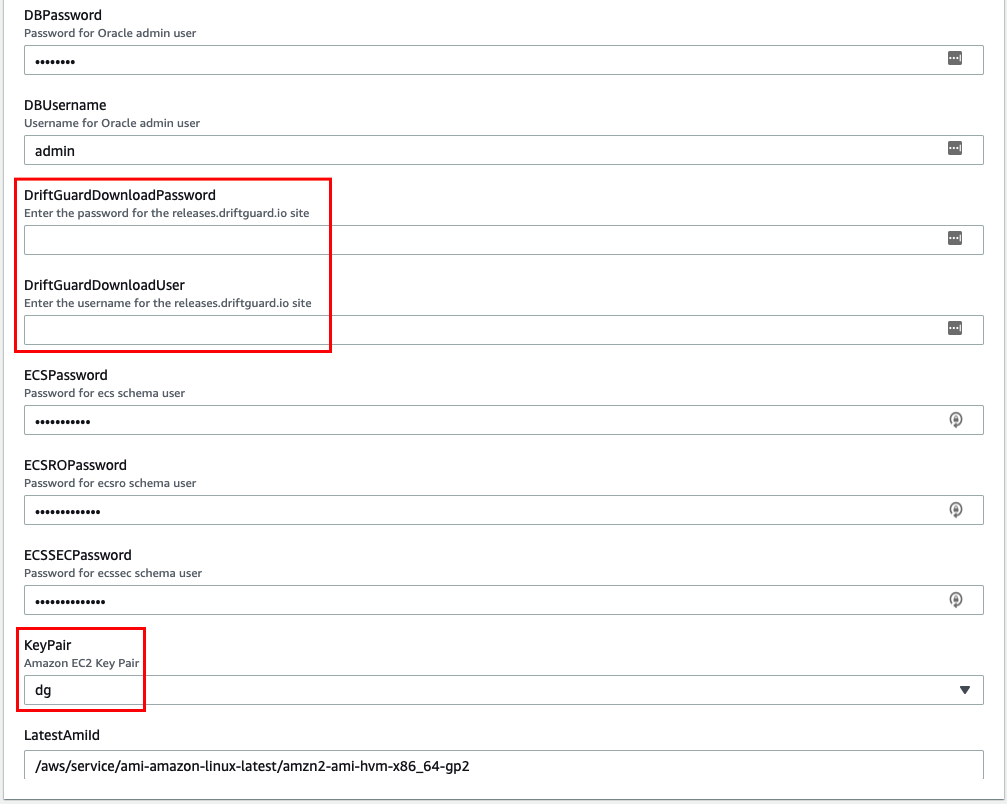
- In the Stack Details screen, enter a Stack name, select an Availability Zone, enter the Download User and Password, and select the dg Key you created earlier – other options can be changed if desired (the provided values can be used as a guide).


- Click ‘Next’ to navigate to the Configure stack options screen – no changes are required here
- Click ‘Next’ to navigate to the Review screen
- Click ‘Create stack’ to begin stack creation – the process will take around 15 minutes
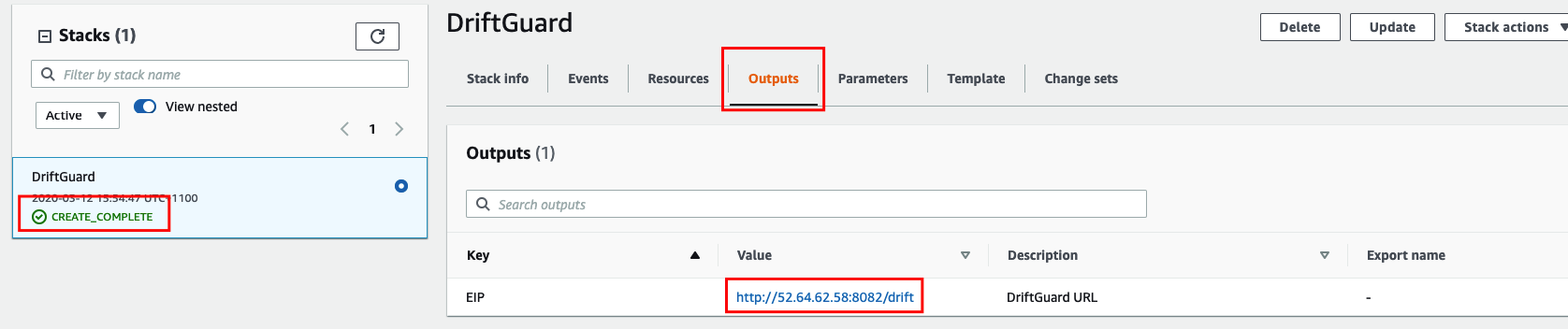
- Once the overall Stack status changes to CREATE_COMPLETE, click the Outputs tab to retrieve the DriftGuard URL

Log in
- Navigate to the DriftGuard URL retrieved from the Outputs tab
- Use the credentials drift / password to log in, at which point you will see a valid licence is not installed (a valid licence must be purchased from LimePoint)
- Once a valid licence is uploaded, full access to the application is provided
Summary
The steps above demonstrate how easy it is to use a CloudFormation template to deploy DriftGuard to the AWS Cloud. Once you are comfortable with the basic setup, it’s a simple matter to go through the process again using settings in the Stack Details screen that are suitable for your company’s needs.
As per the previous blog, configuration of the application is required at this point in order to perform data collection against your target hosts. This is not covered in this post, however, is explained in great detail in the documentation, and may also be covered in a future post.
Please contact LimePoint directly if you have any enquiries relating to DriftGuard, and/or how to leverage the AWS cloud to quickly and simply get started with monitoring configuration drift at your site.
Appendix
---
Parameters:
LatestAmiId:
Type: AWS::SSM::Parameter::Value
Default: /aws/service/ami-amazon-linux-latest/amzn2-ami-hvm-x86_64-gp2
AvailabilityZone:
Description: Amazon availability zone
Type: AWS::EC2::AvailabilityZone::Name
KeyPair:
Description: Amazon EC2 Key Pair
Type: AWS::EC2::KeyPair::KeyName
DriftGuardDownloadUser:
Description: Enter the username for the releases.driftguard.io site
Type: String
AllowedPattern: ".+"
DriftGuardDownloadPassword:
NoEcho: true
Description: Enter the password for the releases.driftguard.io site
Type: String
AllowedPattern: ".+"
DBInstanceID:
Default: driftguard
Description: My database instance
Type: String
MinLength: 2
MaxLength: 63
AllowedPattern: "[a-zA-Z][a-zA-Z0-9]*"
ConstraintDescription: >-
Must begin with a letter and must not end with a hyphen or contain two
consecutive hyphens.
DBName:
Default: dg
Description: DriftGuard Database
Type: String
MinLength: 2
MaxLength: 64
AllowedPattern: "[a-zA-Z][a-zA-Z0-9]*"
ConstraintDescription: Must begin with a letter and contain only alphanumeric characters.
DBInstanceClass:
Default: db.t3.micro
Description: DB instance class
Type: String
ConstraintDescription: Must select a valid DB instance type.
DBAllocatedStorage:
Default: 50
Description: The size of the database (GiB)
Type: Number
MinValue: 5
MaxValue: 1024
ConstraintDescription: must be between 20 and 65536 GiB.
DBUsername:
Default: admin
Description: Username for Oracle admin user
Type: String
MinLength: 5
MaxLength: 16
AllowedPattern: "[a-zA-Z][a-zA-Z0-9]*"
ConstraintDescription: must begin with a letter and contain only alphanumeric characters.
DBPassword:
NoEcho: true
Default: password
Description: Password for Oracle admin user
Type: String
MinLength: 8
MaxLength: 41
AllowedPattern: "[a-zA-Z0-9]*"
ConstraintDescription: must contain only alphanumeric characters.
ECSPassword:
NoEcho: true
Default: ecspassword
Description: Password for ecs schema user
Type: String
MinLength: 8
MaxLength: 41
AllowedPattern: "[a-zA-Z0-9]*"
ConstraintDescription: must contain only alphanumeric characters.
ECSROPassword:
NoEcho: true
Default: ecsropassword
Description: Password for ecsro schema user
Type: String
MinLength: 8
MaxLength: 41
AllowedPattern: "[a-zA-Z0-9]*"
ConstraintDescription: must contain only alphanumeric characters.
ECSSECPassword:
NoEcho: true
Default: ecssecpassword
Description: Password for ecssec schema user
Type: String
MinLength: 8
MaxLength: 41
AllowedPattern: "[a-zA-Z0-9]*"
ConstraintDescription: must contain only alphanumeric characters.
Outputs:
EIP:
Description: DriftGuard URL
Value: !Sub |
http://${MyEIP}:8082/drift
Resources:
MyDB:
Type: "AWS::RDS::DBInstance"
Properties:
AvailabilityZone: !Ref AvailabilityZone
DBInstanceIdentifier: !Ref DBInstanceID
DBName: !Ref DBName
DBInstanceClass: !Ref DBInstanceClass
AllocatedStorage: !Ref DBAllocatedStorage
Engine: oracle-se1
EngineVersion: 11.2.0.4.v23
LicenseModel: license-included
MasterUsername: !Ref DBUsername
MasterUserPassword: !Ref DBPassword
StorageType: gp2
VPCSecurityGroups:
- !GetAtt SSHSecurityGroup.GroupId
MyInstance:
Type: AWS::EC2::Instance
Properties:
AvailabilityZone: !Ref AvailabilityZone
ImageId: !Ref LatestAmiId
InstanceType: t2.medium
KeyName: !Ref KeyPair
SecurityGroups:
- !Ref SSHSecurityGroup
Tags:
- Key: "Name"
Value: "DriftGuard"
UserData:
Fn::Base64: !Sub |
#!/bin/bash -xe
# give the network a chance to finish setting up
sleep 15
# get the latest CloudFormation package
yum update -y aws-cfn-bootstrap
# start cfn-init
/opt/aws/bin/cfn-init -s ${AWS::StackId} -r MyInstance --region ${AWS::Region} || error_exit 'Failed to run cfn-init'
# Start cfn-signal to the wait condition
/opt/aws/bin/cfn-signal -e $? --stack ${AWS::StackId} --resource EC2InstanceCreation --region ${AWS::Region}
Metadata:
AWS::CloudFormation::Init:
config:
packages:
yum:
java-1.8.0-openjdk-devel.x86_64: []
nmap-ncat: []
telnet: []
files:
"/tmp/driftguard.rsp":
content: !Sub |
# DriftGuard Installer Response File
rsp_rootdir='/limepoint/product/drift'
rsp_driftcontextroot=/drift
rsp_drifthttpport=8082
rsp_drifthttpsport=8443
rsp_driftajpport=8081
rsp_driftserverport=8107
rsp_driftlistenaddress='*'
rsp_driftdbhost='${MyDB.Endpoint.Address}'
rsp_driftdbport='1521'
rsp_driftdbconnecttype='1'
rsp_driftdbsid='dg'
rsp_driftdburl='jdbc:oracle:thin:@(DESCRIPTION=(ADDRESS=(PROTOCOL=TCP)(HOST=${MyDB.Endpoint.Address})(PORT=1521))(CONNECT_DATA=(SERVICE_NAME=dg)))'
rsp_driftschemaprefix=''
rsp_driftdbpassword='${ECSPassword}'
rsp_driftrodbpassword='${ECSROPassword}'
rsp_configdb='y'
rsp_driftdbsysusername='${DBUsername}'
rsp_driftdbsyspassword='${DBPassword}'
rsp_driftsecdbpassword='${ECSSECPassword}'
rsp_driftdatafileprefix=''
rsp_configldap='n'
rsp_roleAdmin='RoleAdmin'
rsp_roleDriftAdmin='RoleDriftAdmin'
rsp_roleDriftCollector='RoleDriftCollector'
rsp_roleDriftDeveloper='RoleDriftDeveloper'
rsp_roleDriftViewer='RoleDriftViewer'
rsp_importLdapCertificate='n'
rsp_ignoreCertImportWarnings='y'
mode: "000644"
commands:
1_createUser:
command: "adduser -r driftmgr -d /home/driftmgr -m"
2_moveFile:
command: "chown driftmgr:driftmgr /tmp/driftguard.rsp && mv /tmp/driftguard.rsp /home/driftmgr"
3_addSudo:
command: 'echo ''driftmgr ALL=(ALL:ALL) NOPASSWD:ALL'' | (su -c ''EDITOR="tee -a" visudo'')'
4_setAliases:
command: "echo -e \"alias lr='ls -ltr'\nset -o vi\" >> /home/driftmgr/.bashrc"
5_addEnvVar:
command: "echo 'export JAVA_HOME=/etc/alternatives/java_sdk' >> /home/driftmgr/.bash_profile"
6_createDir:
command: "mkdir -p /limepoint/product"
7_chownDir:
command: "chown -R driftmgr:driftmgr /limepoint"
8_downloadInstaller:
command: !Sub |
runuser -l driftmgr -c 'wget --user ${DriftGuardDownloadUser} --password ${DriftGuardDownloadPassword} -O /home/driftmgr/installer.sh https://releases.driftguard.io/download-dg/latest/driftguard.sh'
9_installApp:
command: runuser -l driftmgr -c 'cd /home/driftmgr && /usr/bin/sh ./installer.sh ./driftguard.rsp'
# wait condition for application installation
EC2InstanceCreation:
CreationPolicy:
ResourceSignal:
Timeout: PT20M
Count: 1
Type: AWS::CloudFormation::WaitCondition
# an elastic IP for our instance
MyEIP:
Type: AWS::EC2::EIP
Properties:
InstanceId: !Ref MyInstance
# our EC2 security group
SSHSecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupDescription: Security Group for DriftGuard
SecurityGroupIngress:
- CidrIp: 0.0.0.0/0
FromPort: 22
IpProtocol: tcp
ToPort: 22
- CidrIp: 0.0.0.0/0
FromPort: 1521
IpProtocol: tcp
ToPort: 1521
- CidrIp: 0.0.0.0/0
FromPort: 8082
IpProtocol: tcp
ToPort: 8082