Features of Modern IAM Platforms
An effective Identity and Access Management (IAM) solution is the cornerstone of any digital security implementation. The most basic function of an IAM platform is to control who has access to what, by maintaining usernames, passwords and permissions, and providing some method of authentication.
Originally IAM solutions focused on Enterprise IAM – enabling employees in organisations to log in to their work environments and access business applications. Now the focus is often more about providing the best possible customer experience and provisioning customer access to online resources, otherwise known as Customer IAM. Real-world solutions need to support both use cases.

Building Blocks
In simplistic terms, there are four basic building blocks at the core of an IAM solution to ensure only validated users can access enterprise data and the resources that they’re entitled to use:
- Identity Governance
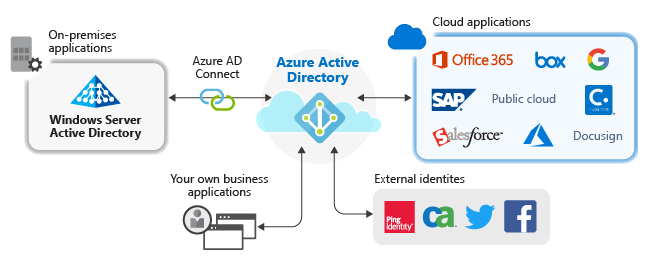
A method to create, read, update, and delete identities in the system. Identities may be user accounts for employees on-boarded via an HR system, or customers who register for a service online. Increasingly, identities can also be things or devices, such as a mobile phone or tablet, that can be associated with a user account. - Identity Repository
A central repository to store information about the different identities, accounts and objects and the relationships between them. The central repository will typically have to be synchronised with data from other connected systems, e.g. an HR system. The repository could be a relational database or, more commonly, an LDAP directory server. - Authentication
Typically IT resources are protected by an access agent installed on either a web server, or a gateway entry point. An authentication server validates user identities and permissions to control access to protected resources. Authentication methods range from basic username and password authentication, to biometric solutions, to integration with 3rd party or social identity providers. User experience is enhanced by providing single sign-on (SSO). Security can also be embellished with services such as multi-factor authentication, session management or password management. - Authorisation
Who has access to what? Authorisation controls what resources a validated user is able to access – for example a customer can only access the services to which they are subscribed. The system could be configured to allow access based on roles, rules, policies, attributes, or even relationships to other objects.
Solution Requirements
So, they are the basics but what constitutes a modern IAM solution?
A typical enterprise IAM infrastructure used to be hosted in closely guarded data centres and required teams of network, platform and IAM specialists to run and maintain. For many reasons, including data sovereignty perceived security risks, cloud adoption has been slower for IAM than for many other IT services. This is rapidly changing, however, with most identity platform vendors now offering cloud deployment options, or full SaaS, cloud-only services, often referred to as IDaaS. Even if not choosing to go with a fully managed service, a modern IAM platform should support deployment on your own private-cloud, hybrid-cloud, and public or multi-cloud, enabling a DevOps deployment model which optionally utilises containerisation and orchestration technologies such as Docker and Kubernetes.
The concept of an identity has evolved beyond employees. Organisations are now managing identities of consumers, customers, business partners, as well as devices, things and services, and the relationships between these various entities. Therefore, in order to support new models required for various digital transformation initiatives, an identity platform needs to provide an extensible object schema mechanism in order to define object types and their relationships to other objects.

As well as basic authentication, your access solution should support various standard authentication and authorisation protocols such as SAML2, OAuth2.0, OpenID Connect and integration with Social Identity providers. You should also expect to see options for enhanced security such as Multi-Factor Authentication (MFA), Captcha, One Time Pin, Email notifications and Knowledge-Based Authentication (KBA). Secondary authentication mechanisms enable features such as self-service password reset and forgotten username retrieval.
Your IAM solution should enforce security protocols easily and consistently across business applications, application programming interfaces (APIs), and microservices. This is typically achieved by deploying a gateway service to act as the enforcement point for the access manager. All components of the IAM platform should provide API support for all identity services and configuration to allow for programmatic management and administration of the system.
The IAM platform has to support identity governance functions to create, read, update and delete identity objects. It is not usually the case that users or objects are created manually in the identity repository – typically accounts are created via synchronisation of data from other connected systems, such as an HR database or other on-boarding mechanism. Customers may also create their own accounts with an online registration process. Accounts created in the identity repository would then need to synchronise out to other connected systems. To achieve these functions, the IAM platform should have a comprehensive and extensible connector framework to enable the 3rd party integrations.
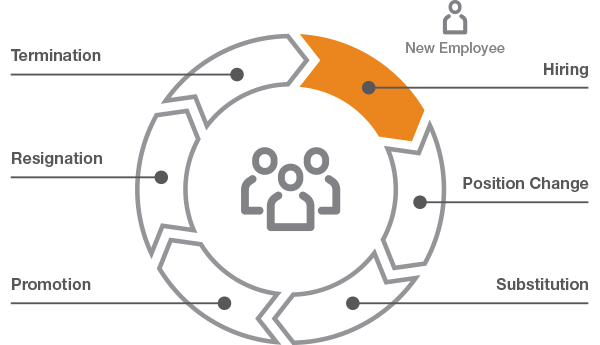
A mechanism to provide user lifecycle management and identity governance workflows will also be required. What is the process that needs to be followed for joiners, movers and leavers? Does the resource owner need to give approval before assigning a role to a user? What actions need to be taken when a customer updates their subscription? The workflow engine needs to be flexible and extensible enough to cater for these types of business workflow requirements.
Some additional things to consider might be options for user self-registration, self-service profile management, password reset, privacy and consent options, linking of social identity providers, and so on. Options to specify terms and conditions, and enforce and record their acceptance. And a comprehensive audit framework across the platform and the ability to monitor platform performance and metrics.
Wrapping Up
Security is paramount, but in the end it’s all about user experience (having your data compromised is not a nice experience), so it is also important that user interfaces for administration and end users are intuitive and easy to use. End users want the security and features offered by a comprehensive IAM solution, but they want it to be as invisible as possible. Whether building and deploying your own platform, or subscribing to a fully managed IDaaS provider, the end goal is to provide security and seamless access for all users wherever they work.